Your challenge
We advise you within a few days regarding your IT security. The service includes the analysis of the current situation, a detailed report with concrete suggestions for improvement as well as the corresponding presentation.
We will be happy to take your individual requirements into account in our customized offer.
Comprehensive overview
Comprehensive overview of the state of information security in your company
Benchmark
Benchmark against organisations in the same industry
Recommendations
Coordinated recommendations to sustainably increase information security
What is tested?
- Infrastructure and network
- Applications
- Data and information security
- Terminal devices
- Cloud solutions
- Security governance
- Permission and access management
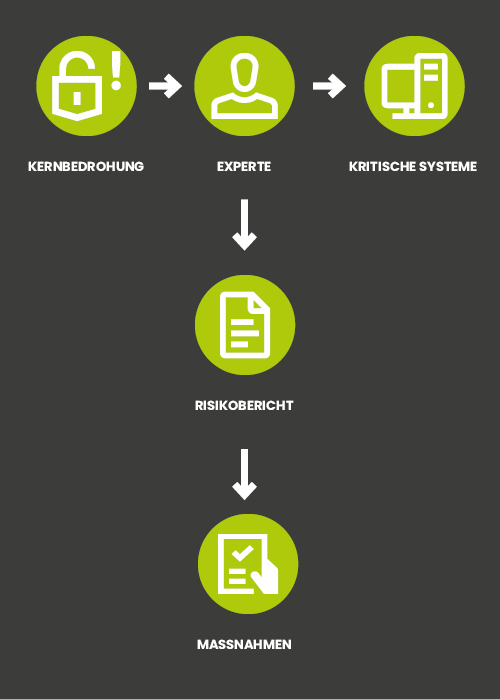
Procedure
In the following, we will show you how an assessment normally works and which processes we go through in the process
1. Initialisation
a. Recording your needs b. Scheduling
2. Identifying security vulnerabilities
Checking your systems for vulnerabilities
3. System and architecture review
Based on interviews, reviewing documents and checking your systems
4. Vulnerability report and action plan
Preparing a vulnerability report and a corresponding action plan as a management summary
5. Follow-up
Verifying the results found once the measures have been implemented
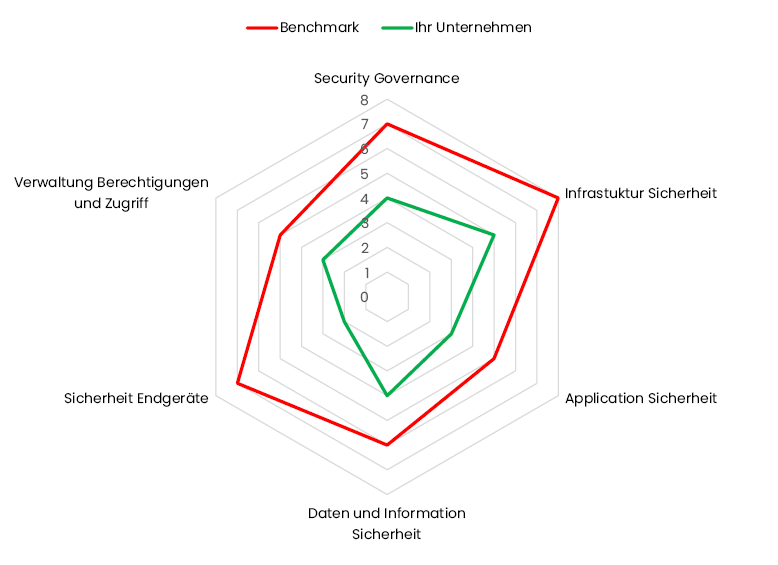
Benchmark
Example of a graphical representation of the presentation of results
