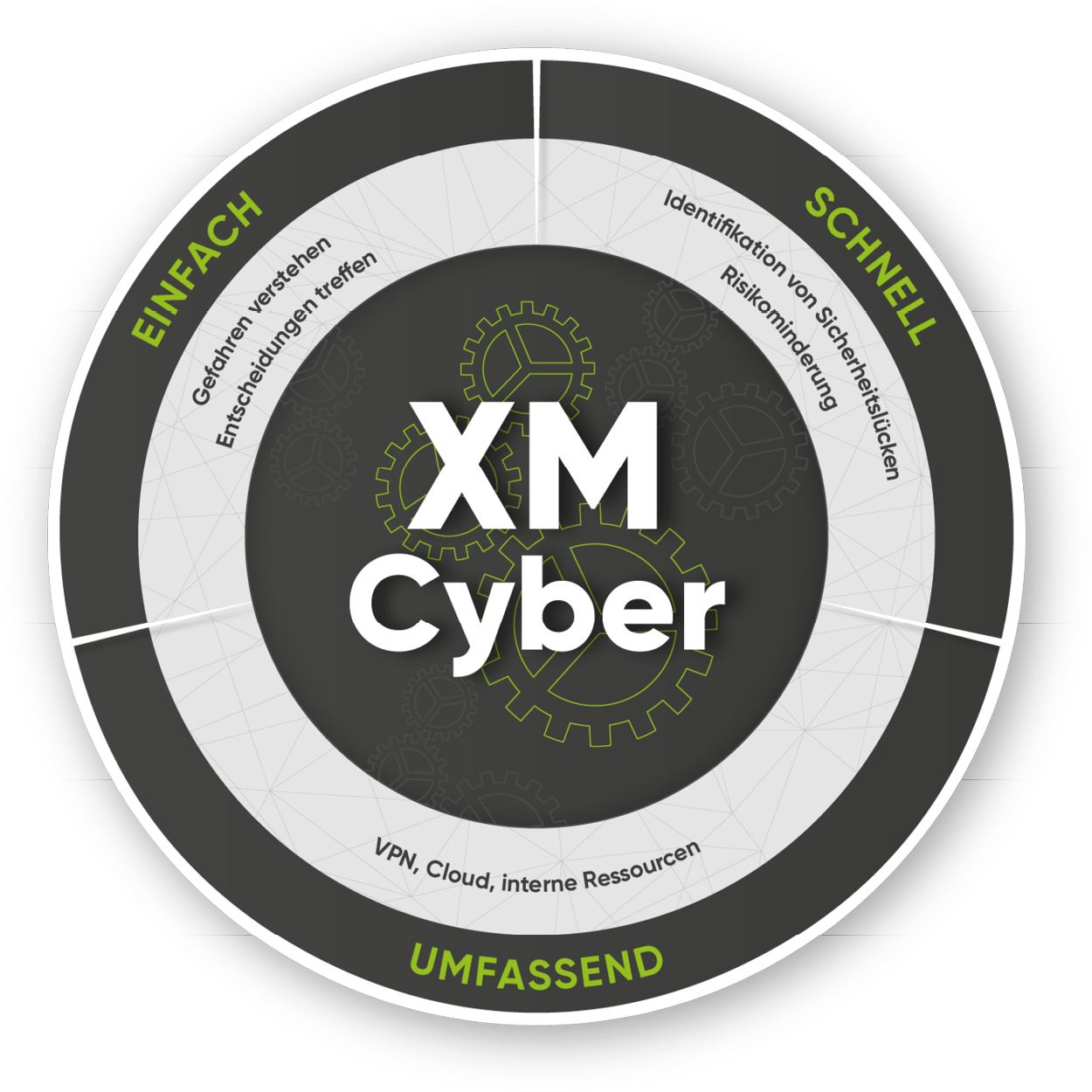
Attack Path Management mit XM Cyber
Unlike other tools you have been using for breach and attack simulation, XM Cyber models your IT infrastructure and continuously checks whether and how an invader could reach your critical resources once he has compromised one of your systems. At a glance, you will be able to identify relevant attack paths, and XM Cyber will tell you exactly where to take action in order to prevent attacks.

By pressing the play button, a YouTube video is loaded and you consent to the transmission of data to Google. Google's privacy policy applies: https://policies.google.com/privacy
Savings from Attack Path Management Deployment at a Glance:
Your benefits with XM Cyber
Automated Breach&Attack Simulation
real-time security posture and threat assessment
no manpower required
proactive security through early detection
Comprehensive analysis of your IT landscape
without any impact on availability
always up to date and on point
clear presentation of real risks
Guidelines for fixing vulnerabilities
XM Cyber will prioritize identified vulnerabilities using different criticality criteria
helps you to quickly and easily improve the security posture of your IT infrastructure
provides you with a roadmap for advanced measures
Ideal for embedding into your overall security management
easy integration into hybrid infrastructures
can be used in combination with third-party components for endpoint security, SOAR, ticketing and vulnerability management
raises the security level by taking into account different components and dependencies
Combat attacks and identify risks
The Swiss IT Security Group offers tailored service packages for XM Cyber. Our experts will not only help you find the perfect solution. We will also implement the system for you, operate it for you if desired, and make sure you get the best value out of it.
Overview Service Packages
Setting up XM Cyber is the first step towards attack prevention: Our service suite Managed XM Cyber is available in four tiers, covering basic setup, configuration, and training whilst our top tier offers 24/7 monitoring and remediation.
Onboarding
Tenant-Management
Bronze
Expert training
Silver
Remediation-Management
Integration into IT security processes
Gold
Download
Are you interested in our solution? You can find detailed field reports as well as the scope of services at a glance in our documents.
